Celebrity AI Imposters Are Coming For Your Bank Account
When technology turns your favorite stars into fraudsters
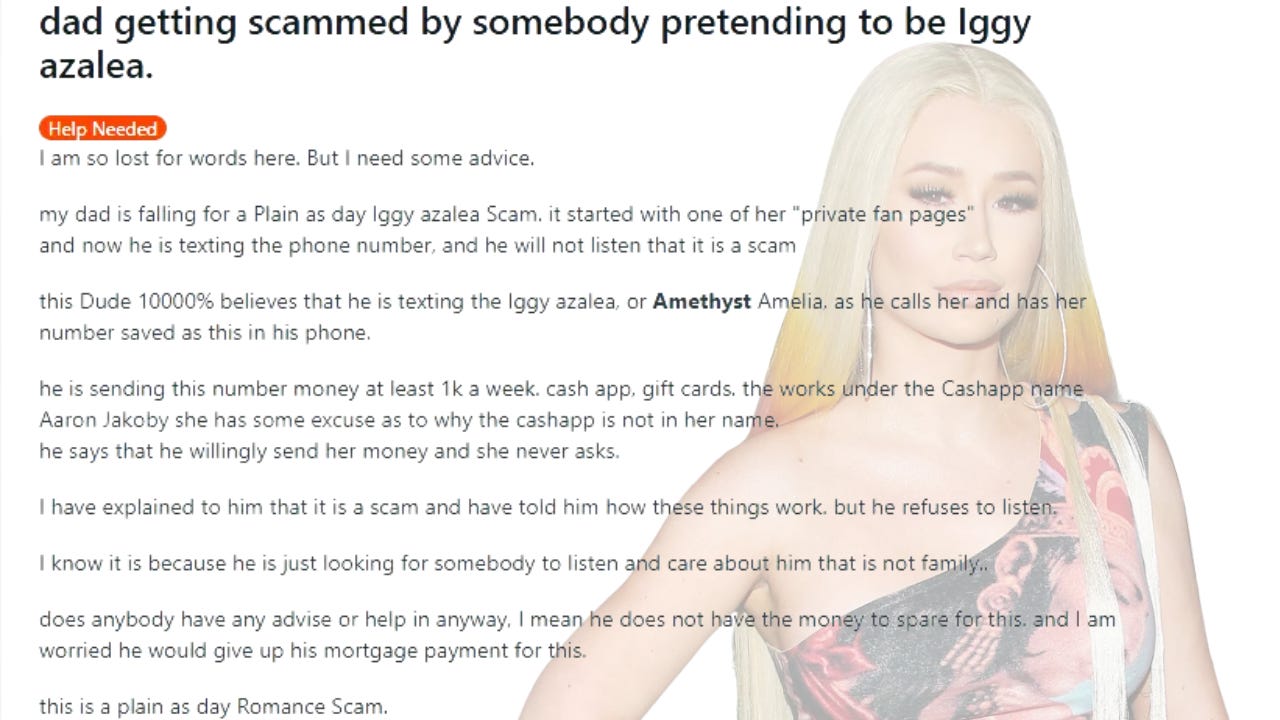
Here’s a wild story we found on Reddit.
A Redditor recently posted how his father thinks he is in a long distance relationship with pop star Iggy Azalea. That’s concerning enough, but the dad is also sending the pop star $1K per week. Here’s the story in the poster’s own words.
This is where most readers say some variation of “how can someone be that &$^$% dumb?”
Fair question, and we doubt our readers would ever fall for a scam like this. You’re in the top 1% of the population when it comes to privacy and scam awareness.
But this isn’t about you. This is about protecting your friends and family.
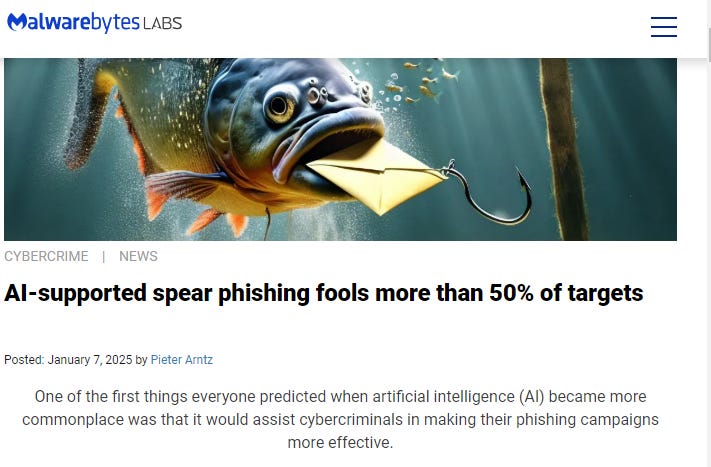
50%+ of the general population already falls for AI spear phishing scams. And that’s just a standard AI phishing scam. Throw in the allure of a celebrity combined with the latest AI tricks plus access to big data, and the odds are surely worse. Which all means this is an issue that we need to take seriously and tackle proactively.
Celebrity Scams: A Growing Problem
Imagine receiving a message from your favorite Hollywood star, asking for help with a personal crisis. It could be a medical issue or a tax issue.
It sounds far-fetched, but for some unfortunate victims, this scenario has become all too real. Take, for example, the recent case of a French woman who was scammed out of an incredible 830,000 euros (approximately $860,000) by someone she believed to be Brad Pitt. The scammer, using AI-generated images and videos, convinced her that "Brad" needed financial assistance for cancer treatment.
Unfortunately, this isn't an isolated incident.
In the United States, the Federal Trade Commission (FTC) has received nearly 200 complaints from individuals who reported being targeted by fake accounts pretending to be actor Johnny Depp. These scams often play on people's emotions and admiration for celebrities, creating a false sense of intimacy and urgency. The amounts people were sending to fake Johnny Depp are incredible. Read about them here. 👇


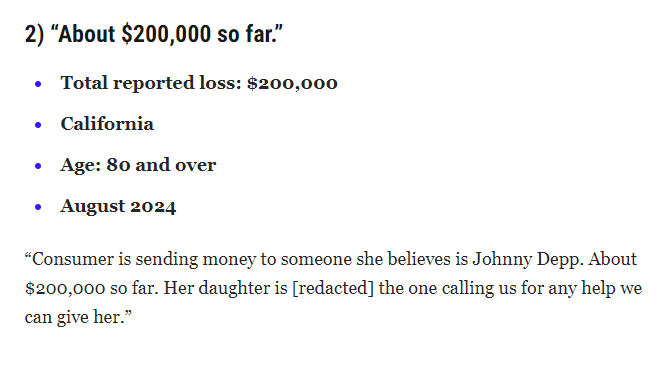

In September 2024, authorities arrested five individuals in Spain for impersonating Brad Pitt online and scamming two women out of $350,000. The fraudsters used sophisticated techniques to build trust with their victims, exchanging messages and emails until the women believed they were in a romantic relationship with the Hollywood star.
The Rise of AI in Scamming
So, how are scammers pulling off these increasingly convincing celebrity impersonations?
Romance scams have been around forever. But they usually involved random people that managed to create carefully contrived “sparks” with their victims. AI is making it easier to add another layer of authenticity combined with an enticing celebrity. Here are some specific ways:
Deepfake Technology: Scammers can now create highly realistic videos and images of celebrities using AI, making it difficult for victims to distinguish between what's real and what's fake.
Voice Cloning: With just a short audio clip, AI can replicate a person's voice with startling accuracy. This technology allows scammers to create fake voice messages or even conduct phone calls posing as celebrities.
Natural Language Processing: AI-powered chatbots can now generate convincing text messages and emails that mimic a celebrity's writing style, making written communication seem more authentic.
Personalized Targeting: AI algorithms can analyze publicly available data to create highly tailored scams that exploit individual vulnerabilities.
This is a privacy newsletter, so let’s talk a bit about that last point – personalized targeting using easy access to personal data.
The Role of Personal Privacy in Modern Scams
Individual pieces of information might seem harmless when shared separately, but criminals can assemble these fragments into a comprehensive picture of their targets. This "Mosaic Effect" occurs when scattered bits of data are combined to create revealing profiles that enable sophisticated, personalized attacks. AI and general tech advancements make this process more seamless and effective.
Cybercriminals commonly exploit several categories of personal data, including::
Basic identifiers: name, address, phone number, and email
Financial details: bank account numbers and purchase history
Government-issued information: Social Security numbers, driver's licenses
Professional data: employment history and work associates
Personal life details: family members, interests, and daily routines
How Scammers Exploit Personal Information
When personal details are readily accessible online, scammers can:
Easily identify potential targets
Tailor their approaches to seem more credible
Craft personalized messages that resonate with victims
Exploit known interests, habits, or vulnerabilities
For example, if a scammer discovers your recent job change on LinkedIn, they might create a convincing phishing email posing as your new company's HR department. Similarly, knowledge of your hobbies or recent purchases could be used to design enticing fake offers or investment opportunities. A pre-existing interest in Johnny Depp makes you more susceptible to a scammer impersonating the actor.
Common Sources of Data
Data Brokers and Public Records
Data brokers collect and sell personal information, often legally, from public records, social media profiles, and other online sources. This information includes names, addresses, employment history, family members, and even voter registration details. Cybercriminals can purchase this data to:
Craft Convincing Scams: With detailed personal information, scammers can create highly personalized and convincing phishing emails or messages, making it more likely for victims to fall for the scam.
Identity Theft: Personal data is used to impersonate individuals, open fraudulent accounts, or apply for loans and benefits in someone else's name.
Social Media Oversharing
Social media platforms are treasure troves of personal information. Users often share details about their lives, interests, and even personal milestones. Most people post videos and photos online. Some will link to podcasts they’ve done. Scammers can exploit all this data and the more they have the better:
Social Engineering: Scammers use this information to craft targeted scams, such as romance or confidence scams, where they build trust with victims before exploiting them financially.
Account Takeover: By gathering enough personal details, fraudsters can attempt to take over social media accounts, using them to spread scams or gather more information about the victim's contacts.
Data Breaches and Leaks
Data breaches expose vast amounts of personal information, which can be sold on the dark web:
Financial Fraud: Stolen data often includes financial details, enabling direct financial fraud or the creation of synthetic identities for further scams.
Account Takeover: With login credentials from breaches, scammers can access accounts, change passwords, and lock out legitimate users.
Malware and Phishing
Malware and phishing attacks are designed to steal personal information:
Web Skimming: Malicious code on websites captures personal data entered by users, including credit card details.
Phishing: Scammers use personal information to craft convincing emails or messages, tricking victims into revealing more sensitive data or downloading malware.
How to Protect Yourself from AI-Powered Celebrity Scams
While the sophistication of these scams is overwhelming to many, there are steps your loved ones can take to protect themselves. If you suspect a scammer is targeting a friend or family member, you can use some of these to build a case and present to them. Particularly #4 and #7
Be Skeptical of Direct Messages: Remember, real celebrities rarely, if ever, reach out to fans directly. Be extremely cautious of any unsolicited messages claiming to be from an alleged celebrity.
Watch for Red Flags: Be wary of requests for money, personal information, or anything that seems too good to be true. Legitimate celebrities don't need to ask fans for financial help.
Use Reverse Image Search: If you receive images purporting to be from a celebrity, try using a reverse image search to see if they've been manipulated or taken out of context.
Check Official Websites: If a celebrity is promoting a product or charity, verify the information on their official website or social media accounts.
Be Aware of AI Limitations: While AI can create convincing images and videos, there are often subtle inconsistencies. Look for unusual skin tones, lighting issues, or strange shadows that might indicate a deepfake.
Education and Awareness: Stay informed about the latest scamming techniques and share this knowledge with friends and family, especially those who might be more vulnerable to such scams.
Trust Your Instincts: If something feels off about an interaction, even if you can't quite put your finger on why, it's better to err on the side of caution.
We provided advice and solutions for defeating general (i.e. non-celebrity) AI driven scams in an earlier post. The best protection is to make yourself a hard enough target that scammers move onto easier prey. How do you do that? Start with this post:
And if you haven’t already, you can grab a free copy of our guide on how to Spot and Avoid AI Scams. New subscribers get an automatic download link for the guide. Existing subscribers can message us for a download link.
Another great privacy move is upgrading to a paid subscription to Secrets of Privacy. To help you out, we’re offering 30% off a one year subscription. Offer is only available until January 31, 2025. Existing paid subscribers can extend their subscription at the discounted price. Get started directly below (or here). 👇
Thank you for your continued support and trust in us. Especially all of our paid subscribers - we couldn’t do this without you. 🙏
Looking for help with a privacy issue or privacy concern? Chances are we’ve covered it already or will soon. Follow us on X and LinkedIn for updates on this topic and other internet privacy related topics. We’re also now on Rumble and YouTube. Subscribe today to be notified when videos are published.
Disclaimer: None of the above is to be deemed legal advice of any kind. These are *opinions* written by a privacy attorney with 15+ years of working for, with and against Big Tech and Big Data. And this post is for informational purposes only and is not intended for use in furtherance of any unlawful activity.
Privacy freedom is more affordable than you think. We tackle the top Big Tech digital services and price out privacy friendly competitors here. The results may surprise you.
Check out our Personal Privacy Stack here.
Online photo storage is a privacy trap. Get the low down on how to store your photos in a privacy friendly way here.
Looking to De-Google your life? Proton is one of the best ways to get there. Get started here with a paid plan for around $1/month. (affiliate link)
If you’re reading this but haven’t yet signed up, join the growing Secrets of Privacy community for free and get our newsletter delivered to your inbox by subscribing here 👇