How Decentralized Edge Technologies Can Redefine Privacy in the Digital Age
Harnessing Local Processing, Caching, and Storage for Enhanced Security and Compliance
Executive Summary: As tech giants intensify data collection efforts, decentralized edge technologies offer a promising alternative for protecting user privacy. This post explores how edge computing, caching, and storage can process data closer to its source, reducing exposure of sensitive information while maintaining performance. Through a look at the implementation and patents of a leader in this space, we show how these technologies can reshape data privacy and compliance in the digital age. For organizations and individuals alike, edge technologies represent a practical path toward enhanced privacy without sacrificing functionality.
Reader Note: This is the first in a new series on emerging privacy tech. These are technologies that have high potential but low general public awareness. To help us out on the tech side, we enlisted the help of Big Dog 1111, an expert in the field of cryptocurrency and emerging technologies like edge computing.
The race to collect data—especially personal information—shows no signs of slowing down. Tech giants like Google have reintroduced controversial techniques such as digital fingerprinting, which can identify users by analyzing device-specific traits. This method stands in stark contrast to privacy-focused regulations like GDPR and CCPA, which prioritize data minimization and user consent.
Fortunately, there is an alternative to funneling every piece of user data through centralized cloud servers: decentralized edge technologies. These approaches—including edge computing, edge caching, and edge storage—process or store data closer to its source, reducing latency, saving bandwidth, and most importantly, enhancing privacy.
What Is Edge Computing—And Why Does It Matter?
Edge computing is a framework that processes data locally, on devices such as sensors, smartphones, or industrial equipment, rather than sending raw information to distant data centers. This design:
Minimizes data travel and reduces latency.
Cuts cloud bandwidth costs by doing more work at the “edge.”
Enhances privacy by limiting exposure of sensitive data.
Think of edge computing like a neighborhood grocery store versus a massive central warehouse. Just as it's more efficient to grab milk from your local store rather than driving to a distant warehouse, edge computing processes data closer to where it's needed. When you use face recognition to unlock your phone, the analysis happens right on your device instead of sending your facial data to distant servers. This local processing not only makes the unlock faster but also keeps your biometric data more private and secure.
Similar examples appear throughout our daily lives: smart home devices processing voice commands locally, modern cars analyzing sensor data for immediate safety decisions, and retail stores using edge computing for real-time inventory management—all while keeping sensitive data close to home
Beyond Computing: Edge Caching and Edge Storage
While edge computing focuses on processing data locally, edge caching and edge storage take this concept further. Edge caching places copies of frequently accessed data closer to end-users, reducing load times and reliance on central servers. Edge storage enables local, decentralized file storage—often with sharding techniques—to safeguard data privacy and integrity.
Theta Network: A Prime Example of Edge Caching, Edge Computing, and Edge Storage
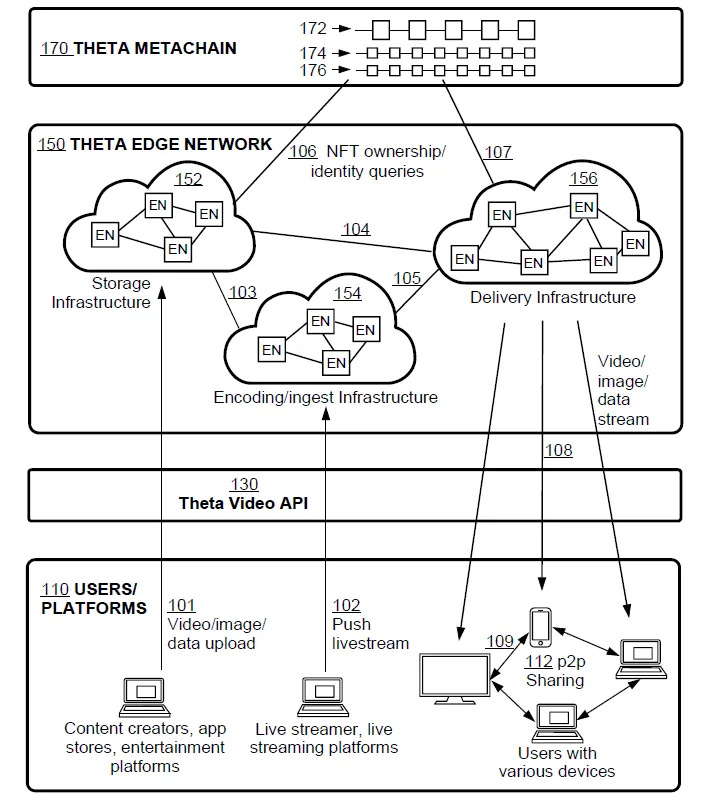
A leader in the decentralized edge ecosystem is Theta Network, which merges these three pillars—edge caching, edge computing, and edge storage—within a robust, token-incentivized framework. Below is an overview of Theta’s architecture and some of their patents related to cutting-edge decentralized technologies.
1. Decentralized Edge Network
Theta’s Edge Network consists of over 10,000 globally distributed Edge Nodes, preventing centralized points of failure and reducing the risks posed by large-scale breaches. Distributing tasks and storing content across many nodes makes unauthorized access significantly more difficult.
2. Theta Labs’ Patents
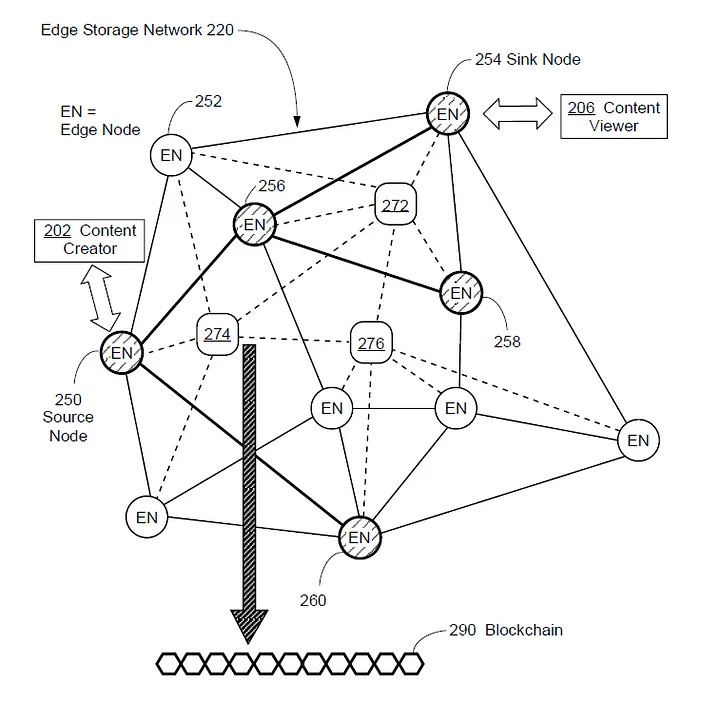
Decentralized Edge Storage Network with Flexible File Sharding (Patent No. 11,611,615 B1)
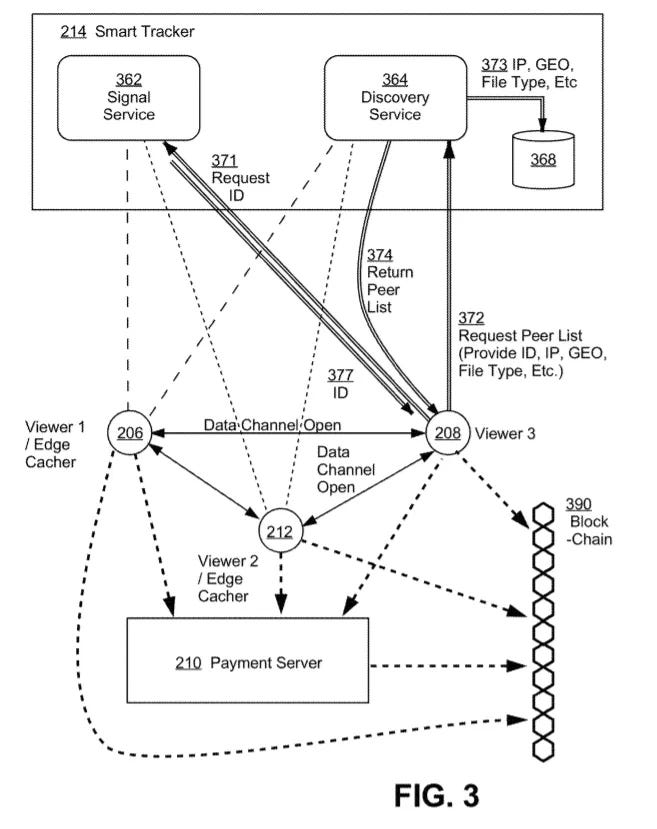
Introduces methods for decentralized storage by splitting files into multiple portions (shards) and distributing them across peer storage nodes. This approach calculates “distances” between file shards and storage nodes based on their identifiers, optimizing for both efficiency and security.Methods and Systems for Data Caching and Delivery over a Decentralized Edge Network (Patent No. 11,153,358)
Describes a hybrid network that combines peer-to-peer connections with a content delivery network (CDN). Edge Nodes receive caching instructions from a tracker server, downloading and storing data fragments for rapid delivery to viewers. This system adapts dynamically to content popularity and node performance, ensuring efficient, secure data delivery.Edge Computing Platform Supported by Smart Contract Enabled Blockchain Network (Patent No. 11,763,332)
Outlines a decentralized edge computing platform where tasks are registered on a blockchain via smart contracts. Edge nodes handle computational tasks through peer-to-peer connections, with solutions verified on-chain or off-chain. Token rewards are distributed upon verification, promoting a collaborative, resource-sharing ecosystem
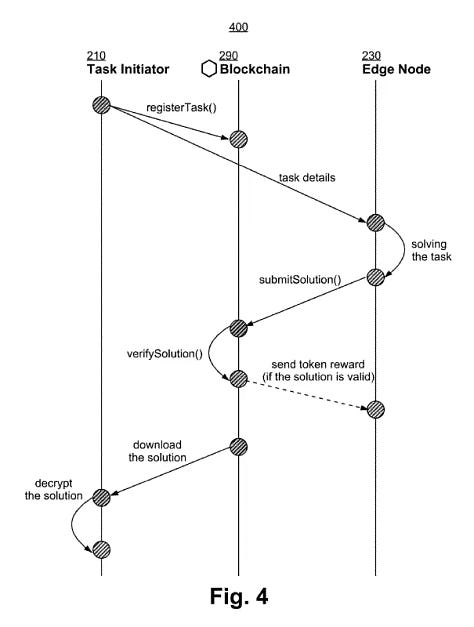
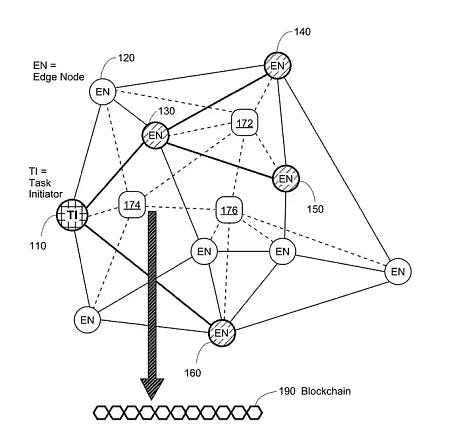
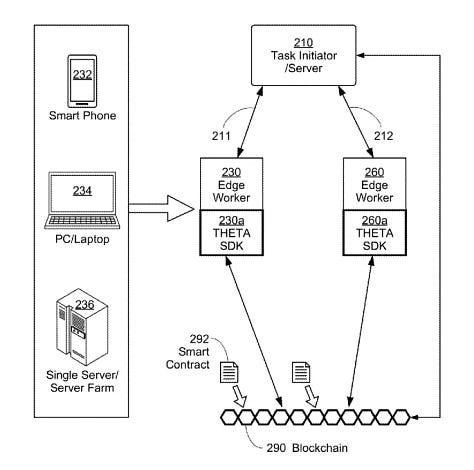
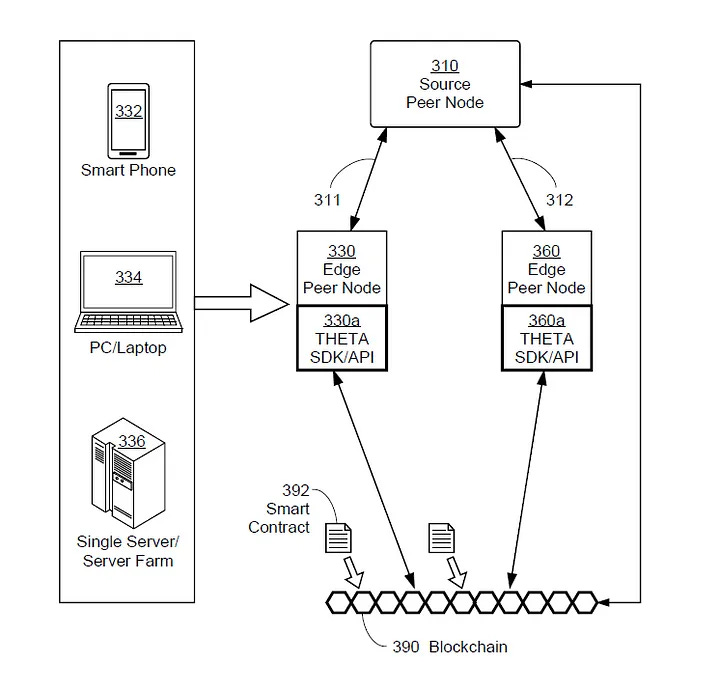
3. Edge Node Operations and Rewards
Theta uses a resource-oriented micropayment pool, enabling Edge Nodes to receive off-chain payments for caching, computing, or storage services. This aligns incentives for network participants and supports a self-sustaining ecosystem. Nodes communicate with tracker servers to receive updated caching or computing directives—so popular or critical data remains primed for quick access and efficient processing.
4. Secure Sharding and Local Processing
Beyond caching, Theta Network (and decentralized networks more broadly) often utilize sharding and local data processing:
Sharding for Enhanced Security: Splitting files or data into multiple encrypted shards means that even if one shard is compromised, it represents only a fraction of the overall dataset.
Data Localization: Keeping data near its source adheres to data sovereignty rules and reduces risk during transit, helping meet regulatory demands like GDPR more naturally.
How Edge Technologies Support Privacy and Compliance
Reduced Exposure of Sensitive Data
By cutting down on long-distance transfers, there are fewer opportunities for malicious interception. Large-scale breaches become less likely when data resides in distributed “chunks” or is processed locally.Regulatory Alignment
Processing data at the edge diminishes compliance headaches with privacy laws. If sensitive information never leaves its originating locale, it avoids the complexities of cross-border data transfers.Resilience Against Centralized Breaches
A single hack into a major cloud provider can compromise millions of records. With decentralized edge setups, would-be attackers face a fragmented, globally distributed network—reducing the payoff of any single target.Real-Time Decision Making with Privacy
Edge AI can analyze data locally—like detecting equipment malfunctions or interpreting voice commands—without sending raw user data to the cloud, preserving confidentiality and saving bandwidth.
Interested in learning more about the Theta Network? Check out the Theta Network Medium Blog, available here.
Case Study: Malong Technologies
Malong Technologies offers a compelling example of edge computing's role in protecting privacy while solving real business challenges. Their RetailAI® Protect system uses advanced AI for loss prevention at self-checkout lanes, processing video feeds locally on edge devices powered by Nvidia's EGX platform. This local processing approach ensures that sensitive surveillance footage remains within the store's premises, eliminating the need to transmit or store customer video data in the cloud.
The system demonstrates the practical benefits of edge computing in retail environments. Using high-definition cameras positioned over self-checkout stations, RetailAI® Protect identifies common issues like mis-scans and ticket-switching in near real-time. By processing this data at the edge, the system maintains customer privacy through automatic obfuscation of people in the video feeds, regardless of age, gender, or ethnicity. This privacy-first approach, combined with edge computing's low latency, allows the solution to scale effectively across thousands of stores without compromising performance or customer privacy.
Cryptocurrencies and Edge Privacy
Decentralized networks, including Theta, Bitcoin, and privacy-focused coins like Monero and Zcash, rely on distributed ledger technology (DLT) to validate transactions without a central authority. This approach can mitigate privacy concerns by eliminating single points of surveillance or failure:
Monero uses ring signatures and stealth addresses to obscure transaction details.
Zcash employs zero-knowledge proofs to verify transactions without revealing sensitive information.
Theta extends DLT principles to content delivery, compute, and storage—ensuring greater security and user autonomy.
Privacy Coins 101
🔒 Curious about privacy coins and how they protect your financial freedom? In this issue, we break down what privacy coins are, how they safeguard your transactions from prying eyes, and why they matter in today's digital age.
Key Challenges for Decentralized Edge Solutions
While these solutions offer numerous benefits, they are not without obstacles:
Device Security: Large, dispersed node networks require strong encryption and secure boot protocols to protect physically accessible hardware.
Data Fragmentation: Sharding and local storage can complicate big-picture analytics if not well-orchestrated.
Implementation Costs: Specialized hardware (e.g., Trusted Execution Environments, secure enclaves) and advanced software can be expensive upfront.
Scalability: Managing and coordinating thousands of distributed nodes demands sophisticated consensus algorithms and infrastructure.
A Future Built on Decentralized Edge Privacy
Whether you're an individual concerned about personal privacy or an organization bound by regulatory demands, decentralized edge solutions offer a compelling path forward—one that doesn't sacrifice functionality for security. Looking ahead to the next few years, several key developments are likely to accelerate this transformation:
AI-Enhanced Edge Processing: As AI models become more efficient, we'll see more sophisticated processing happening directly on smartphones and IoT devices, from real-time language translation to health monitoring—all while keeping personal data local.
Industry Adoption: Traditional sectors like healthcare and finance are expected to embrace edge computing for HIPAA and financial compliance.
Consumer Privacy Tools: We'll likely see a new generation of consumer-focused edge computing tools, from privacy-preserving smart home hubs to decentralized social media platforms that store personal data locally
For organizations looking to get ahead of this trend, consider these initial steps:
Audit your current data processing architecture for opportunities to implement edge computing
Pilot edge computing solutions in privacy-sensitive areas of your operations
Engage with privacy-focused edge computing providers and open-source projects
Be sure to hit the subscribe button and also subscribe to Big Dog 1111 for updates on this topic and related privacy enhancing technologies. Please also follow Big Dog on X here.
Thank you for your continued support and trust in us. Especially all of our paid subscribers - we couldn’t do this without you. 🙏
Looking for help with a privacy issue or privacy concern? Chances are we’ve covered it already or will soon. Follow us on X and LinkedIn for updates on this topic and other internet privacy related topics. We’re also now on Rumble and YouTube. Subscribe today to be notified when videos are published.
Disclaimer: None of the above is to be deemed legal advice of any kind. These are *opinions* written by a privacy attorney with 15+ years of working for, with and against Big Tech and Big Data. And this post is for informational purposes only and is not intended for use in furtherance of any unlawful activity.
Privacy freedom is more affordable than you think. We tackle the top Big Tech digital services and price out privacy friendly competitors here. The results may surprise you.
Check out our Personal Privacy Stack here.
Discover the very real privacy risks of AI chat bots here.
Looking to De-Google your life? Proton is one of the best ways to get there. Get started here with a paid plan for around $1/month. (affiliate link).
If you’re reading this but haven’t yet signed up, join the growing Secrets of Privacy community for free and get our newsletter delivered to your inbox by subscribing here 👇







