What Are Your Photos Telling Strangers?
The hidden data in your images, and how it can be used against you
You finally decide to sell that old couch.
It’s been sitting in your living room for years, and you could use the extra cash. You snap a few photos with your phone, write up a short description, and post it to Craigslist.
A couple of days later, someone texts you asking for more pictures. You take a few extra shots and send them over. They lowball you, you decline, and that’s the end of it.
Except it isn’t.
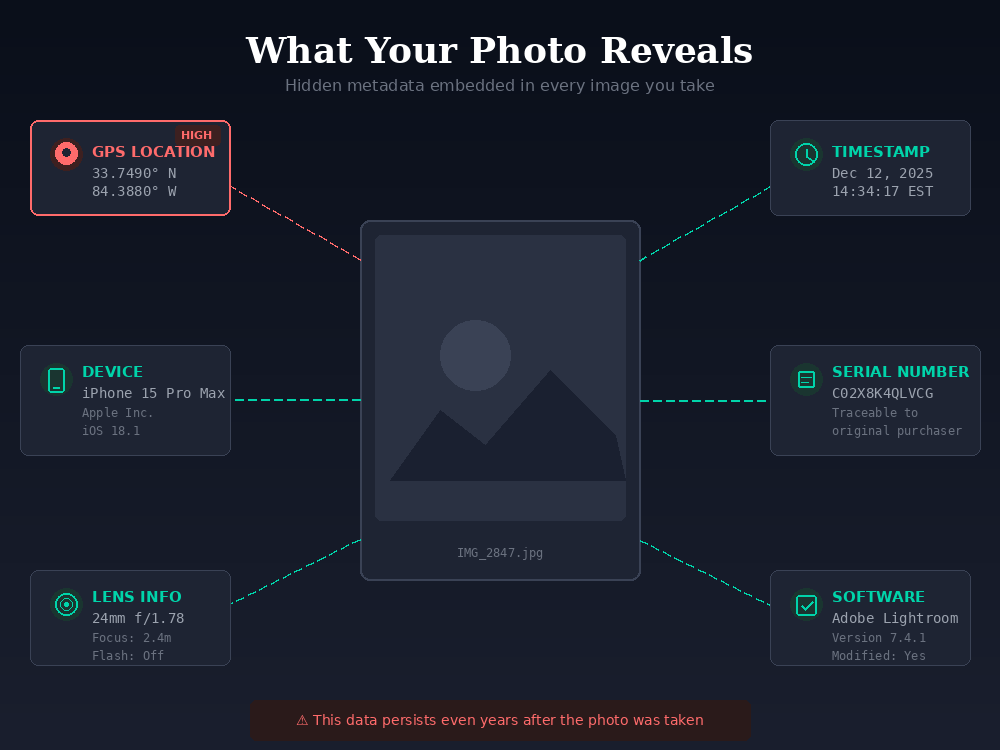
Buried inside those photos you texted was a set of GPS coordinates accurate to within a few meters. It also recorded the date and time down to the second, confirming you were home on a Tuesday afternoon. It captured the make and model of your phone, along with a unique device identifier that could be traced back to you as the original purchaser.
The person who texted you (a stranger you’ve never met) now has all of it. Your home address. When you were there. What kind of phone you own. They could have extracted every detail in seconds using free tools available to anyone with an internet connection.
You thought you were just selling a couch. You had no idea your photos were saying so much more.
What Is Photo Metadata?
Metadata is hidden information automatically stored inside files by your device.
Every photo you take, every video you record, every document you create carries invisible tags that describe when, where, how, and sometimes by whom they were made.
For photos specifically, this information is stored in formats called EXIF (Exchangeable Image File Format), IPTC (International Press Telecommunications Council), and XMP (Extensible Metadata Platform). Your camera or phone embeds this data automatically, often without any indication that it’s happening.
Think of metadata as an invisible receipt attached to every file. Only this receipt contains far more detail than you’d ever want a stranger to see.
What Your Photos Are Telling the World
When you (or a stranger) extract the metadata from a single photograph, here’s what it can reveal:
The exact date and time the photo was created, down to the second.
The camera model, camera name, and model ID.
The camera’s serial number (a unique identifier that can be traced back to the original purchaser).
The lens type, lens ID, and lens serial number.
Flash details including whether it was on or off, its intensity, and the mode used.
The distance between the camera and the subject. Any software used to edit or modify the file afterward.
And the most critical piece: precise GPS coordinates of where the photo was taken.
Even years later, the file still preserves the exact location. Anyone with the data can easily pinpoint on a map the precise spot where someone stood when they pressed the shutter button.
Video Metadata: Even More Revealing
Many people assume videos are somehow “safer” because they’re harder to analyze. The opposite is often true. Videos typically contain everything photos do, plus additional layers of information.
Video metadata can include audio device information such as microphone model and recording settings. It captures frame rate, codec, and bitrate details. It records editing software history and version numbers. Duration timestamps show when recording started and stopped, and when the file was later modified. Sometimes embedded audio tracks reveal background conversations, ambient sounds, or other audio the recorder didn’t intend to preserve.
Video files are also larger and more commonly shared via methods that preserve metadata (more on this later), such as email attachments, cloud storage links, and direct file transfers. The convenience of sharing a video often means its metadata travels intact.
Why This Matters
Every digital file you share hands over information that someone with bad intentions can exploit.
Find where you live: If GPS was enabled when you took that photo, your coordinates are embedded in the file. A stalker, a scammer, or someone you rejected on a dating app can pinpoint your home, your workplace, or your daily hangouts without you ever telling them.
Identify and track your devices: Your phone’s make, model, and unique device identifiers are stamped into every image. Someone building a profile on you now knows what you carry in your pocket. Combined with other data, this helps them target you with phishing attacks tailored to your specific device. It also lets them confirm that multiple “anonymous” accounts actually belong to the same person: you.
Learn your routines: Timestamps reveal more than when a photo was taken. Post enough pictures over time, and someone can map out when you’re home, when you’re at work, when you travel, and when your house is empty.
Verify you’re a real target: Metadata helps bad actors confirm that a photo is authentic and unedited. That means the location data is reliable, the timestamps are accurate, and you’re worth pursuing.
The Metadata Paradox: When It Helps You
Recording photo metadata isn’t always bad. There are legitimate, even helpful situations where you want to preserve it. Here are a few common scenarios.
Copyright protection: Metadata proves you’re the original creator of an image. In disputes over intellectual property, your embedded camera information and timestamps serve as evidence of authorship.
Legal disputes: Timestamp and location data can verify your version of events when your word alone isn’t enough.
Alibi verification: Metadata can prove where you were (and weren’t) at a specific time.
Insurance claims: Documenting when and where damage occurred becomes much easier with metadata-rich photos.
Professional photography: Preserving camera settings helps photographers document their portfolio and techniques.
Organization: GPS coordinates in particular are useful for organizing and finding photos. For example, you can search by “Brazil” or “December 2, 2025” to find all photos associated with those queries.
Reverse Image Search Risk
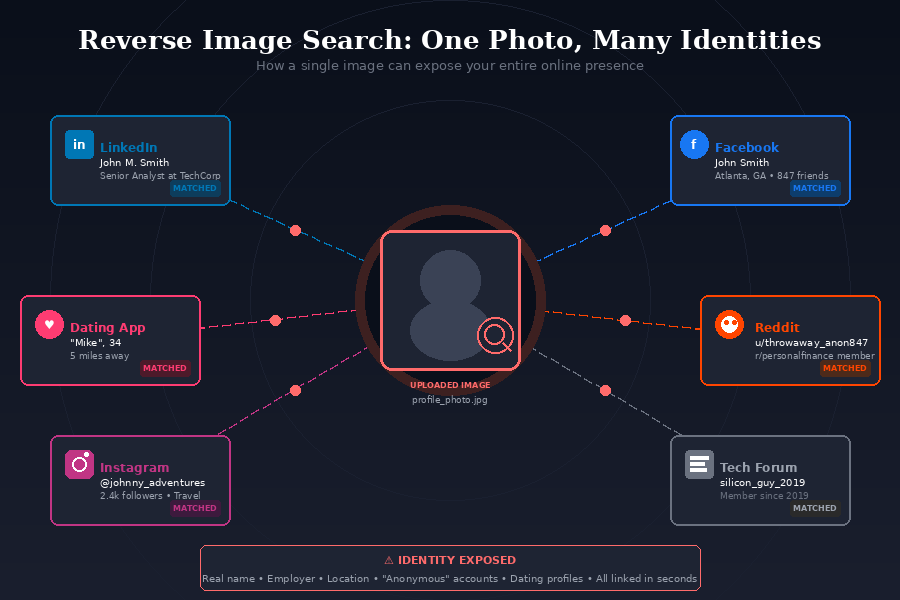
Metadata isn’t the only way your photos can betray you. Reverse image search technology allows anyone to upload a photo and find every other instance of that image (or similar images) across the internet.
Tools like Google Images, TinEye, and Yandex can match your photos across platforms. More concerning are facial recognition search engines like PimEyes, which don’t need metadata at all. Your face itself becomes the identifier.
The Risks Most People Don’t Consider
A single photo can link your anonymous accounts to your real identity. That throwaway forum account with a profile picture? It might be traceable to your LinkedIn profile in seconds.
Old photos resurface in new contexts. Dating profile pictures get traced back to professional networking sites. Forum avatars connect to social media accounts. Screenshots of video calls can be reverse searched and matched to your online presence.
Even cropped, filtered, or slightly edited photos can be matched by modern algorithms. Horizontal flipping or minor edits don’t fool these systems.
Protection Strategies:
Use different photos across platforms you want to keep separate. Be aware that any public photo becomes permanently searchable. Understand that watermarking or intentional modifications may not prevent matching. Consider that your face is now a searchable identifier in ways it wasn’t a decade ago.
How AI Is Amplifying These Risks
Artificial intelligence has fundamentally changed what can be extracted from your photos, even when metadata has been stripped. Here’s how.
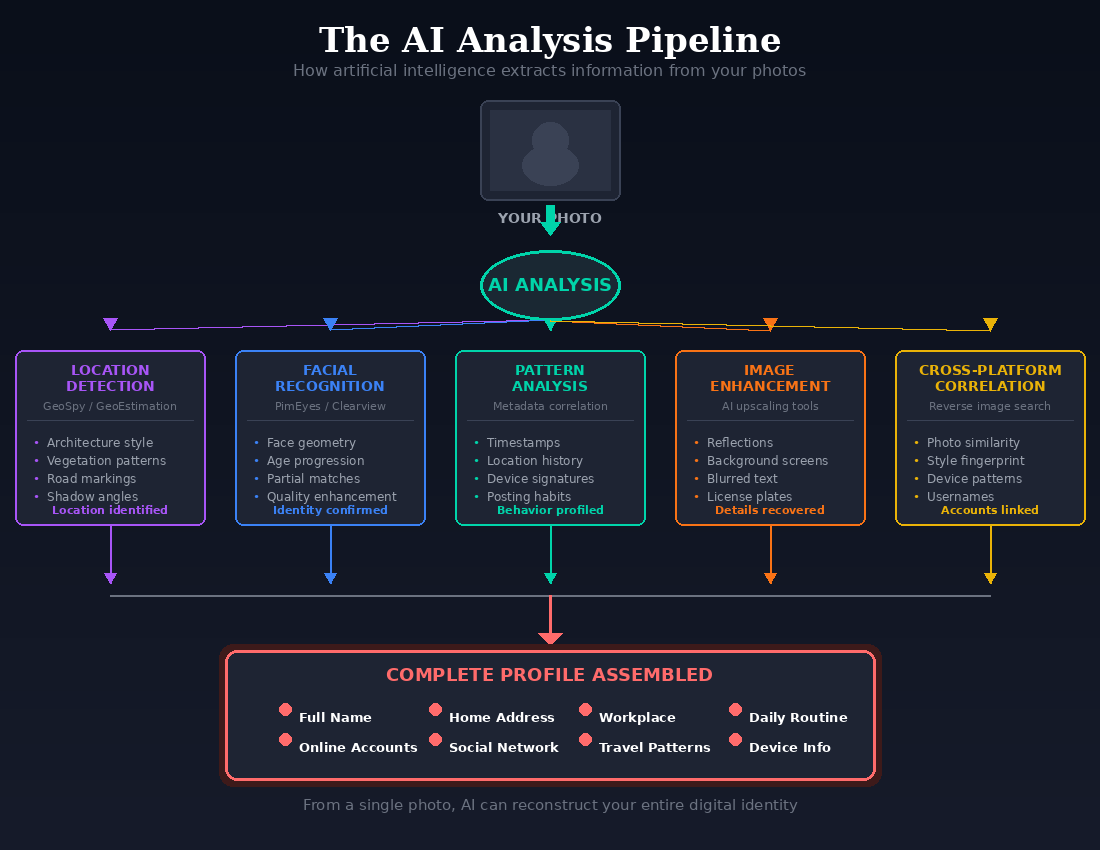
AI-Powered Location Detection
Tools like GeoSpy and similar AI models can identify locations from visual clues alone, with no GPS metadata required. These systems analyze architecture styles, vegetation patterns, signage, road markings, sun position, shadows, power line configurations, even soil color.
A photo with all metadata stripped can still reveal your location through background details you never noticed. That distinctive street lamp, the angle of shadows, the type of trees in the background: AI can process these clues faster and more accurately than any human investigator.

Enhanced Facial Recognition
AI can now match faces across different ages, angles, lighting conditions, and partial obstructions. Low-quality images that were once considered “safe” can now be enhanced and matched. Combined with reverse image search, facial recognition creates powerful tracking capabilities that didn’t exist a few years ago.
Metadata Pattern Analysis
AI can correlate metadata across thousands of your photos to build behavioral profiles. Movement patterns, daily routines, frequently visited locations, device upgrade history, and time-of-day patterns all reveal sleep schedules, work hours, travel habits, and more. Individual photos may seem harmless. The problem is all your photos in the aggregate tells your life story.
Image Enhancement and Recovery
AI can enhance blurred or low-resolution images to extract previously unreadable details. License plates in reflections, screens visible in backgrounds, documents on desks, text on whiteboards: details you thought were too small or too blurry to matter become legible with modern enhancement tools.
Cross-Platform Correlation
AI systems can link your identity across platforms by analyzing photo similarities, posting patterns, and metadata fingerprints. Even without facial recognition, your “photographic style” and device signatures create identifiable patterns.
Key takeaway: Metadata stripping alone is no longer sufficient. The image content itself has become analyzable in ways that weren’t possible just five years ago.
Social Media Platform Policies: Who Keeps What
Most people don’t strip the meta data before sharing photos online. Understanding how different platforms handle your metadata is important for managing your digital footprint.
Platforms That Strip Metadata (From Public View)
Instagram removes EXIF data from public view but retains it internally. Facebook follows the same approach: your friends can’t see your GPS coordinates, but Facebook’s systems can. Twitter/X strips most metadata from displayed images. Snapchat removes metadata from shared content.
Important distinction: These platforms strip metadata for other users. They keep it for themselves.
Platforms That Often Preserve Metadata
Flickr preserves and displays EXIF data by default, as it’s designed for photographers who want that information visible. Google Photos shared links can retain original metadata depending on your sharing settings. Cloud storage services like Dropbox, Google Drive, and OneDrive share original files with complete metadata intact.
Messaging Apps: The Mixed Bag
WhatsApp strips metadata from images. Signal strips metadata by default. Telegram strips metadata when you send as “photo” but preserves it when you send as “file.” iMessage preserves metadata in original quality sends. Email attachments almost always preserve complete metadata.
What Platforms Keep for Themselves
Even when metadata is stripped for public view, platforms typically retain your original GPS coordinates, device identifiers, timestamps, and your IP address at upload time. This data is used for advertising, can be subpoenaed by law enforcement, and may be exposed in data breaches.
The false sense of security: Many users assume “if I can’t see it, neither can anyone else.” Platform privacy policies versus actual data retention practices tell a different story. Your “stripped” photos’ metadata may be exposed years later through data breaches you never anticipated.
Real-World Cases Where Metadata Exposed Everything
Misuse of photo metadata isn’t just a theoretical risk. Below are a few examples of documented situations where photo metadata was used against the person who took or appeared in the photo. We’ll start with one of the most well known examples.
The John McAfee Case
When software pioneer John McAfee was a fugitive, VICE magazine journalists photographed him for a story. The iPhone used to take the photos embedded GPS coordinates in the metadata. Within hours, McAfee’s location in Guatemala was exposed to the world. A single photo from a trusted source compromised his entire effort to remain hidden. (source)
Anonymous Hackers Exposed
In multiple documented cases, hacktivists posting photos to prove data breaches have been identified through metadata. Camera serial numbers get traced to purchase records. Years of careful anonymous activity undone by one image that seemed harmless at the time.
Catfishing and Dating Fraud
Scammers using stolen photos are routinely caught through metadata inconsistencies. Timezone mismatches between metadata and claimed location, device information contradicting claimed lifestyle: these discrepancies reveal deception that wouldn’t be visible from the image alone.
Corporate Espionage
Employees leaking confidential document photos have been identified through metadata that revealed which company phone captured the image. Timestamps correlated with building access logs confirmed who had opportunity. Digital breadcrumbs led directly to the source.
Stalking Cases
Victims have unknowingly shared home locations through social media photos. Real estate listing photos with embedded metadata enabled property identification. Fitness app photos revealed running routes and schedules. In each case, information the victim considered innocuous became a roadmap for those with harmful intent.
Journalistic Source Protection Failures
Leaked documents with metadata have revealed original authors, exposing whistleblowers who believed they were anonymous. Even printer tracking dots (a form of physical metadata) have identified sources of leaked documents. Metadata scrubbing has become essential for sensitive communications, yet many still don’t know it exists.
How to Protect Yourself
Now that you know what your photos can reveal, here’s how to stop them from saying too much. The steps below (organized by phone OS) will help you disable location tracking, strip metadata before sharing, and check what information your existing photos contain.