The Hidden Lesson From the Tea App Data Leak
Millions of messages and photos leaked, proving privacy policies mean little.
Last year we published a piece explaining why reading privacy notices is a waste of time. These documents are too long, too complicated, and (most importantly) often inaccurate. Companies either intentionally mislead you or unintentionally include incorrect information because they don’t fully understand their own data practices. There’s also a lazy factor.
The data leak debacle late last week from the controversial Tea app proved our point in the worst possible way. Let’s find out why.
What Happened
Tea was marketed as a women-only dating safety app designed to protect women when participating in the online dating scene. In practice, it functioned more like an anonymous gossip platform where users could post intensely personal information about other people.
Behind the scenes, the app’s amateur developers were making catastrophic security mistakes. They stored sensitive user data, including selfies, government-issued ID photos, and images from user posts, on an open server that required no password and no encryption. Anyone who stumbled across the address could access everything.
This wasn’t a “hack.” And there was no sophisticated breach. The company simply left its front door wide open. Once the discovery spread online, the entire database was downloaded and shared via torrents. Thousands of people suddenly had access to the information.
What Was Exposed and What Wasn't
What was exposed:
Approximately 72,000 images, including around 13,000 selfies and government-issued ID photos used for account verification, plus another 59,000 images from posts, comments, and direct messages.
Over 1.1 million private messages containing highly sensitive user discussions (e.g., infidelity, abortion, personal contact information).
What was not exposed:
Email addresses, phone numbers, passwords, or other standard account identifiers. TBH, we're kind of surprised none of these were included in the exposed data since they're usually the top things exposed in an incident like this.
Even though login credentials weren’t part of the leak, the scale and sensitivity of the data exposed make this one of the most damaging incidents we’ve seen in the “dating and relationships” app space.
Why Privacy Notices Failed Users (Again)
Tea’s privacy notice contained multiple promises that were completely contradicted by the company’s actual practices. Let’s look at three areas where they failed:
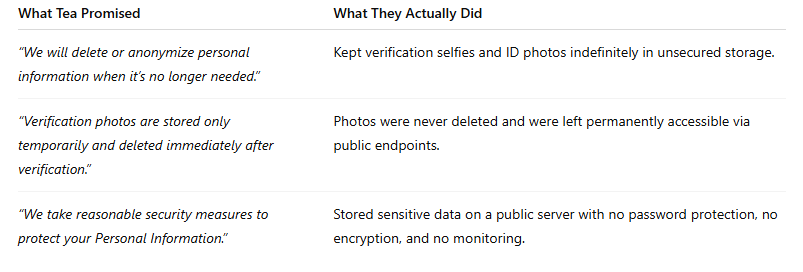
1. False Claims About Data Retention
From their privacy notice:
“We will either delete or anonymize [personal information] or if this is not possible (for example, because personal information has been stored in backup archives), then we will securely store personal information and isolate it from any further processing until deletion is possible.”
Reality: Tea never deleted verification selfies or government-issued ID photos after the registration process. These images were stored indefinitely and were left exposed on unsecured public servers. They were not “isolated,” nor were they encrypted.
2. Misleading Statements About Photo Verification
From their notice:
“This photo is securely processed and stored only temporarily and will be deleted immediately following the completion of the verification process.”
Reality: The opposite happened. These photos were still sitting in publicly accessible endpoints long after accounts were verified. They were never deleted, and there was no “temporary” storage.
3. Vague, Ineffective Security Promises
Also from their notice:
“Tea Dating Advice takes reasonable security measures to protect your Personal Information to prevent loss, misuse, unauthorized access, disclosure, alteration, and destruction.”
Reality: Tea left its most sensitive user data on an open Firebase bucket with no password protection and no encryption. This is the cybersecurity equivalent of leaving boxes of Social Security cards on a park bench.
The privacy notice hedges with “no security measures are impenetrable” language, which is true but irrelevant. Tea’s failure wasn’t due to an advanced cyberattack. Rather, it was about failing to take even basic measures to secure data.
This situation looks to us like a clear case of gross negligence and maybe even willful misconduct.
Translation: Tea is going to get crushed when the lawsuits start rolling.
Here’s a side-by-side look at what Tea promised and what they actually did:
Why This Matters (and Why You Should Care)
It’s easy to shrug off data leaks with a “breaches happen all the time, big deal” mentality. But this particular breach is different because of what was exposed and how it can be exploited.
Deeply personal, highly sensitive content – We’re not talking about credit card numbers or email addresses (which can be replaced or reset). These were intimate photos, government-issued IDs, and private conversations about relationships, infidelity, and trauma. Once those are out in the open, there’s no way to pull them back.
Permanent digital footprint – This data is now circulating on torrent sites and forums. Even if Tea were to disappear tomorrow, copies will live on indefinitely. Years from now, someone could still dig up these images and messages.
Reputation damage, doxxing, and harassment risks – Leaked DMs can be weaponized. Abusive partners, stalkers, and online harassers could use this information to intimidate, blackmail, or publicly shame victims. Private photos, home addresses, and ID details can lead directly to doxxing, stalking, and real-world harassment.
Collateral harm beyond the users – Many of the leaked messages name other people (ex-partners, friends, coworkers). Innocent third parties can now be dragged into the exposure without ever using the app themselves.
This is why breaches like Tea’s matter. Unlike a stolen password, you can’t “reset” your private messages, home address, or verification selfie. The damage is lasting, and the fallout can hit you when you least expect it.
What You Can Do
You can’t control how a company handles your data once you hand it over, but you can take steps to limit the damage if something like this happens again. The key is reducing the amount of sensitive information you share and making yourself harder to track or target.
Assume data you hand over will be stored indefinitely. Even if a company promises to delete it. Once it leaves your possession, it's out of your control. Be prepared for it to enter the public domain. If you’re not okay with that, then think twice about handing the data over.
Minimize the data you provide. Avoid verification methods that require photo IDs unless it’s absolutely necessary. Handing over verification documents for financial services is impossible to avoid. Handing them over for a dating site is more discretionary. Be smart.
Use disposable email addresses and other tools that reduce your digital footprint. While email wasn't a leaked data point here, this is an exception.
If you need help, our Inbox Firewall guide is a great starting point. It teaches you how to set up disposable email addresses so you can cut ties with apps and services when they inevitably disappoint you. (the link gets you 25% off list price)
Our How Exposed Are You Online? guide is another resource worth checking out. It walks you through how much information about you is already out there and how to start cleaning it up. This is our most popular and actionable guide yet.
Bonus: Our Insider Perspective
Unlike most privacy influencers, we’ve actually worked inside the tech industry. We've counseled tech startups and helped acquire others. We know how these policies are written and how casually data is actually handled. We’ve seen the gap between what’s promised and what’s delivered.
Our best guess on what occurred:
Keep reading with a 7-day free trial
Subscribe to Secrets of Privacy to keep reading this post and get 7 days of free access to the full post archives.