The Password Advice Everyone Misses
The case for unique usernames (and a free tool to create them)
You’ve heard it a thousand times: use a unique password for every account.
It’s good advice. But it’s incomplete because people miss the risk of using the same or similar usernames across multiple websites.
Why is that a problem?
Reusing usernames creates two kinds of risk. The immediate one is credential stuffing attacks, which use stolen login pairs to break into your other accounts. The slower one is every shared username is a breadcrumb that connects your profiles across the internet, making it easy for doxxers, stalkers, or anyone with free OSINT tools to build a detailed picture of who you are. Unique usernames shut down both.
Creating unique usernames is difficult, which keeps most people from using this simple tactic. At least it was difficult - until now.
We’re pleased to announce we’ve released a free tool that allows you to create unique usernames on the fly. Read on for more information. First, some important context.
What is Credential Stuffing?
When a company gets breached, attackers don’t just sit on the stolen data. They take those username-password combinations and test them against other sites, such as banks, email providers, shopping accounts.
Why?
The attackers are hoping you’ve reused the same credentials somewhere else.
Credential stuffing is automated, it’s cheap, and it works. Even with a success rate around 0.1%, the math is in the attacker’s favor.
One million stolen credentials can unlock roughly 1,000 accounts. And there’s no shortage of stolen credentials floating around. One leaked collection alone (referred to as “Collection #1-5”) contained 22 billion username-password combinations. (source)
The damage is real.
In 2023, 23andMe suffered a credential stuffing attack that exposed data on nearly 7 million users, which included ultra-sensitive genetic heritage and family connections data. In 2022, PayPal disclosed that 35,000 accounts were accessed the same way, exposing names, addresses, dates of birth, and Social Security numbers. Roku experienced a credential stuffing hack in 2024 which we covered. 👇
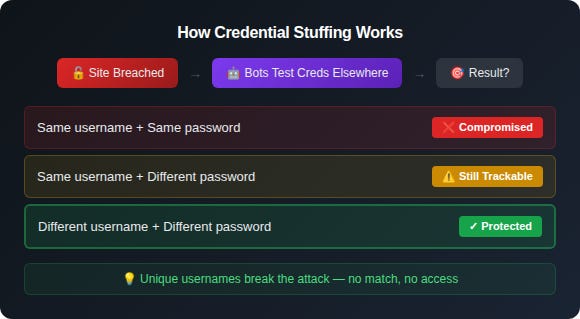
Why Unique Usernames Break The Attack
Credential stuffing requires a match on both username and password.
If your password from a breached site gets tested elsewhere, but you used a different username on that other site, the attack fails. The credentials don’t match, removing you from the crosshairs.
Most people use the same username everywhere, either in the form of an email address (joe.smith@gmail.com) or standalone username (joe.smith). That’s the weak link.
Change the username, and you’ve removed half of what the attacker needs.
The Longer-Term Risk: OSINT and Doxxing
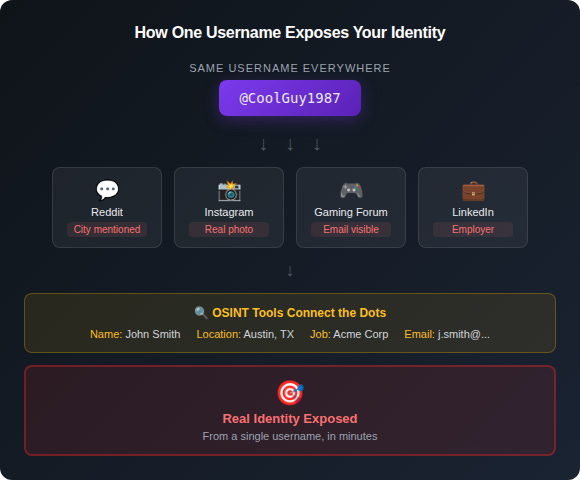
Credential stuffing is the immediate threat. But there’s a slower, more personal risk that comes from username reuse: you’re making yourself easy to track.
There’s an entire discipline called OSINT (Open Source Intelligence) built around piecing together someone’s identity from publicly available information. Username correlation is one of the most effective techniques.
Free tools available online can search for a username across hundreds (even thousands) of platforms in seconds. Enter a handle and instantly see every site where it exists. From there, it’s just connecting the dots: your interests, your location, your real name, your employer.
This is how doxxers operate. A gaming handle leads to a Reddit account. The Reddit account reveals your city. A few more searches and they’ve got your home address, maybe your family members.
And it’s getting worse.
OSINT platforms are now integrating artificial intelligence (AI) to correlate usernames with other identifiers, such as email addresses, profile pictures, writing style, activity patterns. These systems can predict username variations and flag connections that would take a human hours to find (if ever). The barrier to tracking someone down is dropping fast.
If you want to go deeper on how exposed your identity is online, our best selling guide How Exposed Are You Online? walks you through a self-audit using the same OSINT techniques investigators and doxxers use. It covers 8 key exposure areas and links to the tools (many free) so you can see exactly what's findable about you, and fix it. Grab a copy here for only $7 (or free if you’re a paid annual subscriber to the newsletter).
The Fix: A Unique Username For Every Account
We’ve written about best practices for creating usernames before. The challenge is actually doing it.
Coming up with random, unique usernames on the fly is tedious. And if it’s tedious, most people won’t bother.
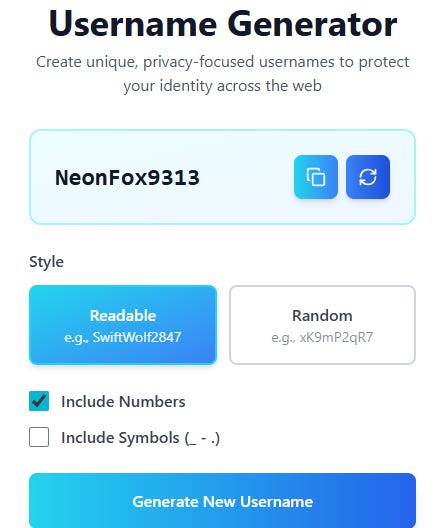
That’s why we built a free username generator tool.
How should you use this tool?
Simple. Generate a unique username, copy it, and save it in your password manager alongside your password. Done.
No tracking. No sign-up. Just a quick way to create usernames that don’t connect your accounts or make you a target.
A few tips:
Generate a new username for every account. Your password manager will remember them. You don’t have to.
Pair it with email aliases. If a site requires an email as your username, use an alias from SimpleLogin, Proton, or similar. Same principle.
Don’t overthink it. The username doesn’t need to be memorable. That’s what password managers are for.
Bookmark the tool. On mobile, create a shortcut for your home screen. On your desktop computer, add a bookmark to your browser for quick access.
This is one of those small upgrades that stacks into a big privacy win over time. You’re blocking credential stuffing attacks and making yourself harder to track. Two benefits, one habit.
Give it a try and let us know what you think.
Any parents of young kids?
We just launched a free mini-course for parents setting up a child’s first iPhone.
Privacy defaults. Screen Time basics. A routine that sticks.
Two ways to get started:
Watch via our digital shop here
Watch on YouTube here (logged out and using Brave to block trackers, of course)
FAQs
1. Is the username generator free?
Yes, completely free. No sign-up, no email required. Access it here.
2. Do you store or track the usernames I generate?
No. The tool runs in your browser. We don't see, store, or log anything you generate. Best practice is to close the tab or refresh the page after you’re done to clear the data from your system.
3. Do I really need a unique username for every account?
Ideally, yes. At minimum, use unique usernames for sensitive accounts like banking, email, healthcare, social media, and anything tied to your real identity.
4. How do I remember all these usernames?
You don't. That's what password managers are for. Store each username alongside your password. Your password manager will then autofill both.
5. What if a site requires my email as the username?
Use an email alias. Services like SimpleLogin, Proton, Apple Hide My Email and DuckDuckGo let you create unique aliases that forward to your real inbox. Same protection, no extra inboxes to manage.
6. Does this actually stop credential stuffing?
Yes. Credential stuffing requires a match on both username and password. Change the username, and the stolen combo can’t work.
Looking for help with a privacy issue or privacy concern? Chances are we’ve covered it already or will soon. Follow us on X and LinkedIn for updates on this topic and other internet privacy related topics.
Disclaimer: None of the above is to be deemed legal advice of any kind. These are *opinions* written by a privacy and tech attorney with years of working for, with and against Big Tech and Big Data. And this post is for informational purposes only and is not intended for use in furtherance of any unlawful activity. This post may also contain affiliate links, which means that at no additional cost to you, we earn a commission if you click through and make a purchase.

Privacy freedom is more affordable than you think. We tackle the top Big Tech digital services and price out privacy friendly competitors here. The results may surprise you.
Do you own a Smart TV? If so, you won’t want to miss this post from our reader favorite post Smart TV Privacy Settings: How to Disable Tracking on Every Brand.
If you’re reading this but haven’t yet signed up, join for free (4.2K+ subscribers strong) and get our newsletter delivered to your inbox by subscribing here 👇




This is so true. I can't tell you how many people I've found based on them using the same username 😭
I’m not a fan of those generated passwords and usernames because I don’t have any control if I need to manually get into my accounts.