He thought he was anonymous. He was wrong.
An anonymous account tried to doxx ICE agents. Now the operator is exposed, under federal investigation, and facing real-world consequences.
For months, an anonymous X account called LAScanner posted real-time alerts about ICE activity in Los Angeles. The updates were specific: unmarked vehicles, alleged agent names, even the hotels where agents were staying.
The account picked up traction, and attention. Not just from supporters, but from people who wanted to find out who was behind it.
This week, they did.
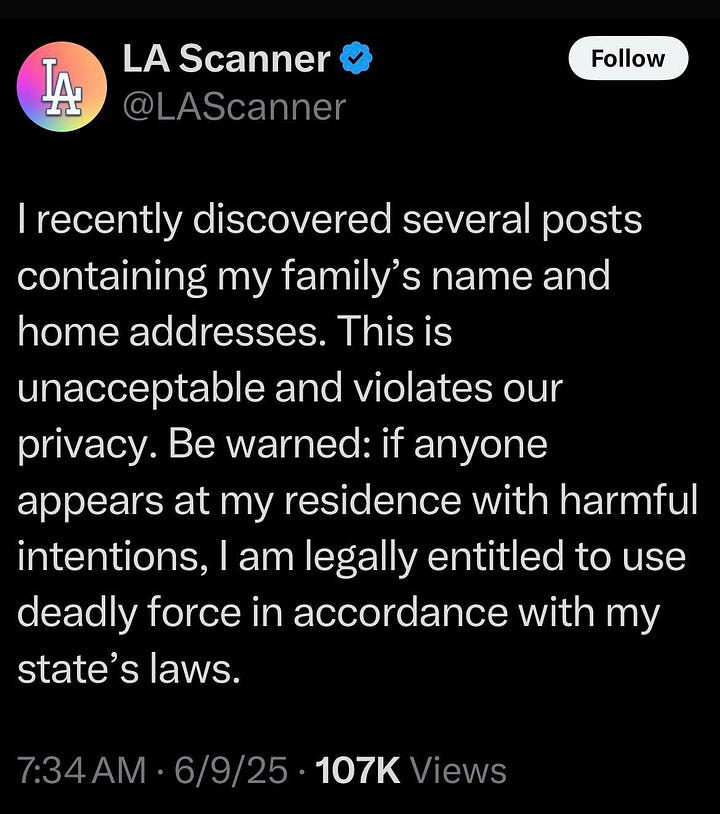
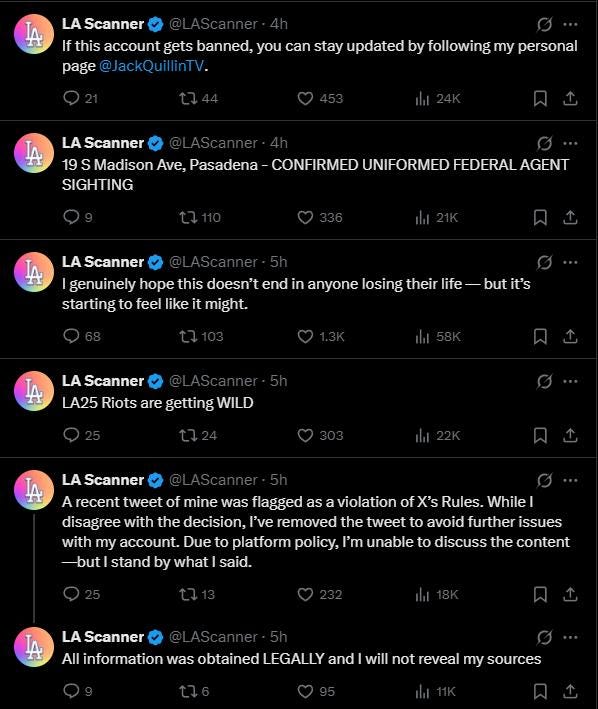
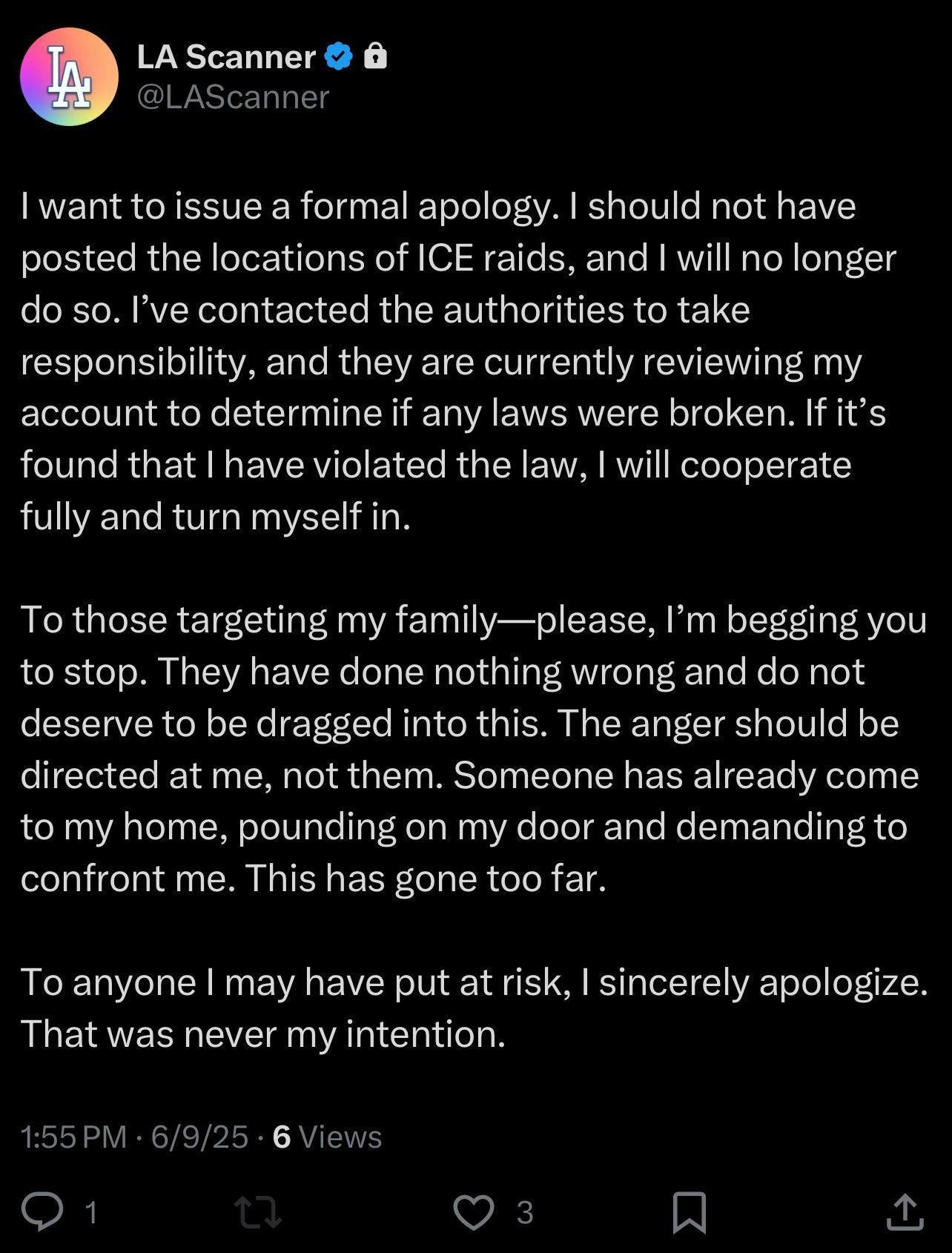
The person behind LAScanner was doxxed. He later posted an apology and said he’s under federal investigation. Jail time is now on the table. Here he is in his own words.
Let’s set aside the politics. Whether you agree with what he was doing isn’t the point. The bigger issue is how this played out from a privacy perspective and what can we learn from this guy’s mistakes?
Doxxing isn’t rare anymore
There was a time when doxxing felt like something that only happened to celebrities or people with massive platforms. That’s no longer the case.
Today, anyone with a grudge, a few tools, and some time can start piecing together your online identity. Entire forums exist just to hunt and expose people. The more controversial or high-profile your activity, the more likely you are to end up on their radar.
They don’t need access to your phone or your email. They just need enough breadcrumbs.
A reused username. A photo with visible landmarks. A comment posted years ago under a different alias. Once something small surfaces, others pile on. The puzzle comes together fast.
And once you’re exposed, there’s no taking it back.
Visibility is a tradeoff
LAScanner made himself a target by the nature of his posts. Publicly tracking law enforcement movements is going to attract scrutiny. Publishing hotel locations of federal agents all but guaranteed someone would try to unmask him.
Whether he understood the risks or just underestimated his exposure, he’s now facing real-world consequences.
He didn’t just lose anonymity. He may lose his freedom.
This is the tradeoff of online visibility. The more reach you have, the more likely it is that someone will look into who you are. That might not matter for a random meme account. But if you’re posting in ways that cross legal or political lines, or gain a sizeable following, you need to assume someone will come looking.
Anonymity is a moving target
Too many people treat anonymity like a checklist: use a VPN, create a burner email, post under a fake name. Done.
But real privacy isn’t a one-time setup. It’s a system. It has to account for habits, mistakes, slipups, and the fact that our online behavior is deeply fingerprintable.
At a certain level, you need to separate identities across devices, browsers, and networks. Proactively strip metadata. Avoid posting styles or patterns that make you easy to identify. Be careful about links, third-party platforms, and anything that could leak identifying data.
It’s not about being perfect. It’s about making it hard enough that someone gives up or never starts.
LAScanner didn’t do that. He got caught. And now he's another case study in what not to do.
Want to learn how to protect yourself from the same fate?
We just released a self-audit tool for evaluating how trackable you are online.
It’s based on the real methods digital investigators use to identify people online, and how you can defend against them (i.e. Opensource Intelligence a/k/a OSINT).
This is a no fluff guide. Just practical, step-by-step advice for making yourself a harder target for doxxers and scammers.
If LAScanner had followed it, there’s a good chance he wouldn’t have been found as quickly.
This OSINT-inspired checklist isn’t just for activists or whistleblowers. It’s for anyone who wants to reduce their exposure, like the business owner who prefers to keep a low profile, the professional who doesn’t want the public digging through their personal history, or the parent who wants to shield their family from stalkers and threats.
📍Get the privacy risk audit here. Annual paid supporters get it for free (DM us if you want a copy). Everyone else can get it for just $7.
Stay sharp. Don’t wait to lock things down until it’s too late.
💥 P.S. If you found this post helpful, please restack it and share it with your friends, family and audience.
This helps spread the words and keeps us writing content that will help you bolster your privacy and become a harder target.
Looking for help with a privacy issue or privacy concern? Chances are we’ve covered it already or will soon. Follow us on X and LinkedIn for updates on this topic and other internet privacy related topics.
Disclaimer: None of the above is to be deemed legal advice of any kind. These are *opinions* written by a privacy attorney with years of working for, with and against Big Tech and Big Data. And this post is for informational purposes only and is not intended for use in furtherance of any unlawful activity.
Privacy freedom is more affordable than you think. We tackle the top Big Tech digital services and price out privacy friendly competitors here. The results may surprise you.
We just published a new guide on how to bulletproof your inbox using disposable email addresses and aliases. It covers the best tools, when to use (and not use) them, and how to combine aliases with other privacy tech for max protection. There are even a few bonuses included. Grab a copy here at the special intro rate of $19. The price will go up at the end of June.
Check out our Personal Privacy Stack here. It’s a simple, easy way to start De-Googleling your life.
AI scams are here and getting more sophisticated. One of the best things you can do to protect yourself is to remove your personal information from Google and the data broker sites. That starves the scammers of vital information, making you a much harder target. You can DIY, or pay a reasonable fee to DeleteMe to do it for you. Sign up today and get 20% off using our affiliate link here. We’ve used DeleteMe for almost five years and love it for the peace of mind. It’s also a huge time saver.
If you’re reading this but haven’t yet signed up, join the booming Secrets of Privacy community for free (2K+ subscribers strong) and get our newsletter delivered to your inbox by subscribing here 👇





It was a great read.
And yeah, it's scary - how you can build a whole profile on someone using OSINT.
People need to be careful about the things they are posting online, because all of it can be used negatively.
If he would have followed OpSec as a life principle there wouldn't be any need OSINT. Truthfully OSINT is part of a broader spectrum that can incorporate Operational Security on multiple layers.
But then again, his actions seem to be depicting the script kiddies level.