A Reader Clicked a Link Shared From Facebook. Here’s What Happened Next.
How Facebook and marketing tools can connect your browsing to your inbox — and the habits that keep you a harder target
A reader recently shared a story with us that’s worth unpacking.
He clicked on a link his wife sent him about a professional service. The link originated on facebook. The next day, the business emailed the reader directly with the line: “Hi, I saw you visited our website.”
The reader hadn’t filled out a form. He hadn’t given this business his email address. So how did the company know who he was?
We almost forgot. This reader wasn't some slouch when it comes to privacy - his stack is top ~10% as we show below.
The Setup
When the reader told us this story, what stood out was how ordinary the situation sounded. His wife found a Facebook ad for a professional service and shared the link over Signal. The reader tapped the link on his phone, skimmed the page, and moved on with his day. No forms were filled out. No information was typed in. Nothing that should have connected his identity to that visit.
And this reader was ahead of 90% of the gen pop. Here’s the setup on his phone:
A de-Googled Android operating system
The Brave browser with standard protections
Signal for messaging
Facebook isolated in a separate browser (DuckDuckGo)
That’s a solid privacy stack. The reader clearly wasn’t acting carelessly. Yet it still wasn’t enough to stop Facebook from handing his identity over when he clicked a link.
What likely happened
At first glance, it feels almost impossible:
how could a simple website click turn into a direct email from the business?
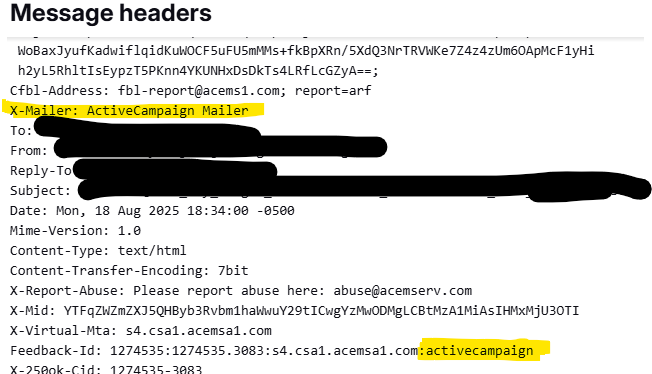
The key detail came from the email itself. It was sent through ActiveCampaign, a popular marketing automation platform that specializes in linking anonymous web visits back to known contacts. Once you know that, the mystery starts to make sense. More on ActiveCampaign in the next section.
How did we find the info about ActiveCampaign? It was buried in the header details of the email. Here's a partial screenshot the reader shared.
Here’s the likely chain of events:
The reader clicked the Facebook ad link (wrapped in Facebook’s tracking redirect).
Even though they opened the link in Brave, Facebook cookies from their DuckDuckGo login were still valid on the device.
Facebook’s Conversion API matched that click back to the reader’s Facebook profile, and by extension, their real email address.
ActiveCampaign tied the visit to a contact record and triggered the automation: “Send an email when this person visits.”
In short: Facebook already had the reader's email and name, and the advertiser’s tech stack closed the loop.
The Role of Marketing Automation Platforms
Here's some insider knowledge you won't get from other privacy influencers since we've been in the business for 15+ years. As long time readers know, we're not hobbyists. We have a legal background with deep experience in tech, SaaS, MarTech, Privacy, and AI.
The company in this story used ActiveCampaign. On the surface, it’s just an email marketing service, the kind that sends newsletters and manages subscriber lists. But under the hood, tools like ActiveCampaign are built to do much more than send bulk emails.
They install tracking scripts on a company’s website that watch who visits, which pages they click, and how long they stay. When the system can connect that activity to an email address (whether through cookies, Facebook’s Conversion API, or data enrichment from outside sources) the visitor is no longer anonymous. They’re a “contact” in the company’s database.
From there, it’s all automated: the platform can tag the contact, score their “engagement,” and trigger emails like “I saw you visited our site.”
ActiveCampaign isn’t alone in this. There’s a whole ecosystem of platforms designed to identify visitors and feed them into sales funnels:
HubSpot. One of the biggest names in customer relationship management (CRM). Tracks web activity, logs email opens, and syncs with ad platforms.
Clearbit. Specializes in “data enrichment.” It takes a small signal (like an IP address or domain) and pulls in personal or company details from large databases.
Leadfeeder. Focuses on identifying companies and individuals who visit your site, even if they never fill out a form.
Wunderkind (formerly BounceX). Known for aggressively matching anonymous website traffic to known emails.
For businesses, these tools promise higher conversions and fewer “lost” visitors. For individuals, it means you can land in a company’s CRM (and their inbox automation) without ever typing your email into their site.
Facebook’s tracking shows how easily your identity can be tied to a simple click. Much of that comes down to the personal information floating around in data broker databases. The less of your data that’s out there, the harder it is for companies (or scammers) to connect the dots back to you.
You can try to remove yourself from those broker sites manually, or you can save a lot of time by using a service like DeleteMe. We’ve used it for almost five years, and it’s been a reliable way to cut down on exposure, reduce spam, and get peace of mind.
If you want to give it a try, you can sign up here and get 20% off through our affiliate link. It’s a quick, high-ROI privacy move and one of the easiest ways to stack a privacy win.
Other Ways This Can Happen
In this story, Facebook’s tracking and ActiveCampaign’s visitor identification features were the most likely culprits. But that’s not the only way companies connect anonymous browsing back to your inbox. Here are several others worth knowing about:
Email tracking pixels. If you’ve ever opened a marketing email from a company, there’s a good chance it carried an invisible pixel that planted a cookie. Later, if you visit their site, that cookie tells their CRM who you are. From there, automations like “send an email when this person returns” can fire instantly.
Link decoration. Links in marketing emails often include hidden identifiers (
?contactId=1234&email=you@example.com). If someone forwards you that link and you click it, their system immediately knows which contact record you belong to, even if you never typed in your email yourself.Data broker enrichment. Services like Clearbit, ZoomInfo, and LeadFeeder specialize in resolving anonymous visits. They look at IP addresses, device fingerprints, or cookies and match them against large datasets of emails and profiles. If your information is in those datasets, a simple page view can be tied back to your inbox.
Retargeting and cookie syncing. Adtech companies run vast networks that share cookies across sites. Even though browsers like Brave block most third-party cookies, retargeting systems can sometimes sync identifiers in the background. If they already know your profile from another site, that identity can follow you to new ones.
Further reading on Facebook privacy issues:
What You Can Do About It
Hearing a story like this can make it feel as if there’s no way to stay private online. But that’s not true. The tools this reader was already using—CalyxOS, Brave, Signal, and DuckDuckGo—put them ahead of most people. The key is adding a few extra habits on top to keep closing the gaps:
Use email aliases. With SimpleLogin, DuckDuckGo Email Protection, or Annon Ady, any “identity match” grabs only an alias, not your main inbox. For more on disposable email strategies to stop spam and scammers, check out our guide The Inbox Firewall. Get it for 25% off here (or free if you’re an annual paid subscriber to this newsletter).